Active Directory Certificate Templates play a pivotal role in establishing a secure and reliable IT infrastructure. By providing a standardized framework for issuing digital certificates, these templates ensure that users and devices are authenticated and authorized to access network resources. In this guide, we will delve into the intricacies of creating professional Active Directory Certificate Templates that exude professionalism and instill trust.
Template Design Elements
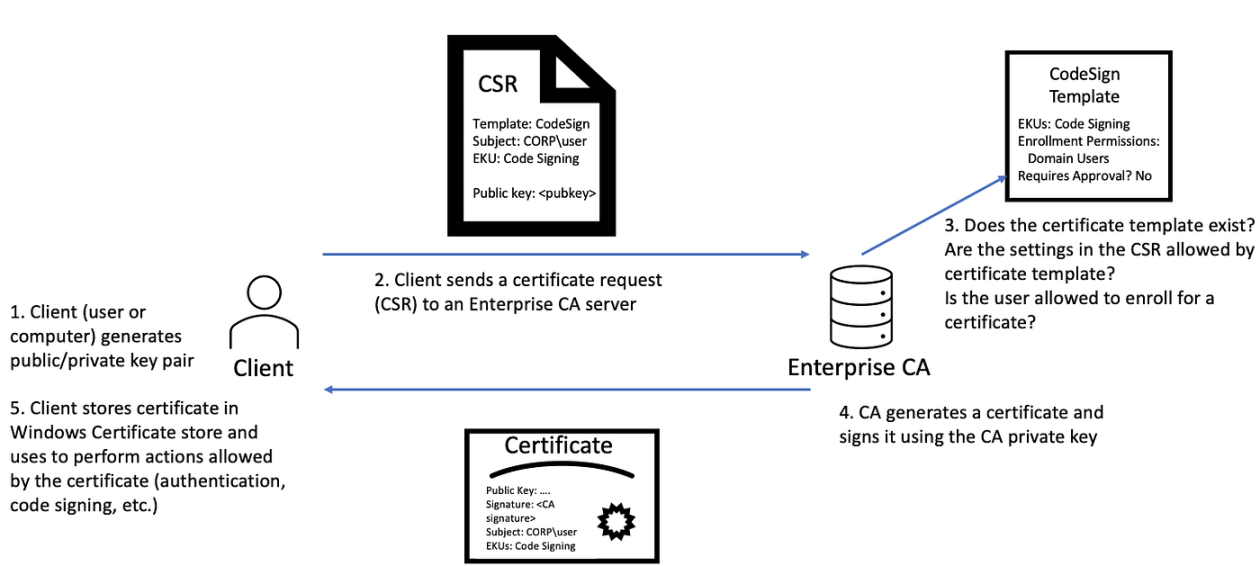
The design of an Active Directory Certificate Template is paramount in conveying a sense of professionalism and credibility. The following elements should be carefully considered:
1. Certificate Name and Description
The certificate name should be concise, descriptive, and aligned with its intended purpose. A well-chosen name provides immediate clarity to users and administrators. The description field offers an opportunity to elaborate on the certificate’s specific use cases and any relevant restrictions.
2. Validity Period
Setting an appropriate validity period is crucial to maintain security and prevent unauthorized access. Consider factors such as the sensitivity of the data being protected and the frequency of password changes when determining the expiration date.
3. Issuing Authority
The issuing authority is the entity responsible for generating and distributing certificates. This information should be clearly displayed on the template to establish trust and accountability.
4. Subject Name
The subject name identifies the entity to whom the certificate is issued. It typically includes the common name (CN), organization (O), organizational unit (OU), country (C), and other relevant attributes. Ensure that the subject name is accurate and consistent with the intended use of the certificate.
5. Key Usage
The key usage field specifies the permitted cryptographic operations for the certificate. Common key usages include digital signatures, encryption, and key encipherment. Select the appropriate key usages based on the security requirements of your organization.
6. Extended Key Usages
Extended key usages provide additional flexibility in defining the certificate’s capabilities. For example, you can specify whether the certificate can be used for client authentication, server authentication, code signing, or email protection.
7. Key Algorithm and Key Length
The key algorithm determines the cryptographic method used to generate the certificate’s public and private keys. Popular choices include RSA and ECC. The key length should be selected based on the desired level of security and the computational resources available.
8. Certificate Policies
Certificate policies are statements that define the operational characteristics of the certificate. They can include information about the issuing authority’s policies, the intended uses of the certificate, and any applicable restrictions.
9. Certificate Extensions
Certificate extensions offer a mechanism to add additional information or constraints to the certificate. Common extensions include subject alternative names (SANs), key usage restrictions, and policy constraints.
Best Practices for Professional Certificate Templates
Consistency: Ensure that your certificate templates adhere to a consistent design language and branding guidelines.
By carefully designing and managing your Active Directory Certificate Templates, you can establish a strong foundation for a secure and efficient IT infrastructure. By following the guidelines outlined in this guide, you can create templates that inspire confidence and trust among users and administrators alike.